DDOS PROTECTION
There is no doubt that DDoS attacks are very irritating, even though they are becoming very common nowadays. These attacks are usually targeted at individual users, businesses or even corporations, and they often have damaging consequences. Nevertheless, with SimpliServers, you have nothing to fear because we provide complete protection and mitigation against DDoS attacks with a single IP capacity of 480+ Gbps.
What a DDOS attack even is?
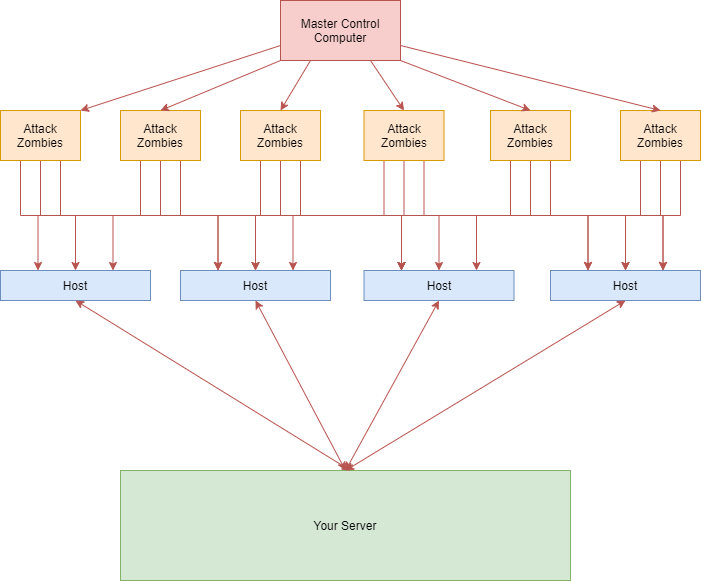
A DDoS attack, which is an acronym for Distributed Denial of Service attack, operates by generating huge sustained amounts of traffic on the targeted network or server. Various compromised computers on different networks over the globe are usually involved in the distribution of the attacks.
A DDoS attack overloads the bandwidth of a server or drains its resources in order to make it inaccessible or unavailable to genuine users. A server or network simultaneously receives a large volume of requests from numerous points across the internet during a DDoS attack. The service becomes unstable or, worse still, unreachable as a result of the intensity of this “crossfire”.
To businesses, DDOS attacks can present loss of sales, lost of internal tools, dissatisfied customers or even total blackout.
Mitigation Technology
Types of DDOS Attacks
There are 3 most common DDOS attacks that could make your site, application or business unavailable to the outside world. These are:
- Bandwidth Attacks: These attacks saturate your network's capacity, rendering server unavailable (SMURF, UDP Flood, ...)
- Resource Attacks: These attacks consume large amounts of server resources, making machine unable to process legitimate requests (IGMP Flood, DNS Flood, ...).
- Exploitation Attacks: These attacks exploit bugs in software running on your server, which tricks the machine into an inability to control itself (Ping of Death, ...).
This is how a typical attack looks like:
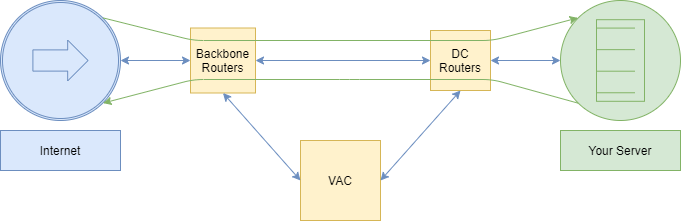
Stage 1: There is no attack
Internet-based services are used without any problem. The traffic passes through the backbone of our network then arrives at the data center. Finally, it is handled by the server that sends back the responses over the internet.
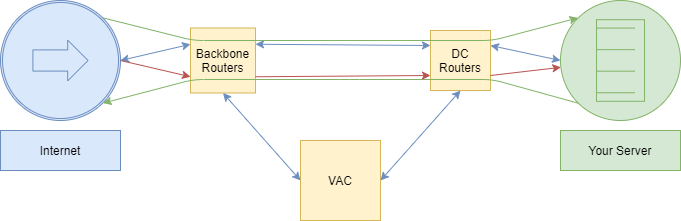
Stage 2: Attack begins
The attack is launched via the internet and on the backbone. Given the surplus capacity of the bandwidth on the backbone, the attack will not cause saturation on any link. The attack reaches the server, which begins to handle the initial attack. At the same time, analysis of the traffic flags that an attack is underway and triggers the mitigation.
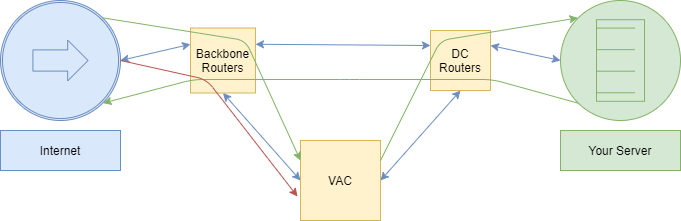
Stage 3: Mitigation
Between 15 and 120 seconds, after the attack has begun, mitigation is automatically activated. Incoming server traffic is vacuumed by the VACs, hosted in OVH data centers. The attack is blocked with no duration or size limit, regardless of type. Legitimate traffic passes through the VAC and arrives at the server. The server responds directly without going back through the VAC. This process is called auto-mitigation.
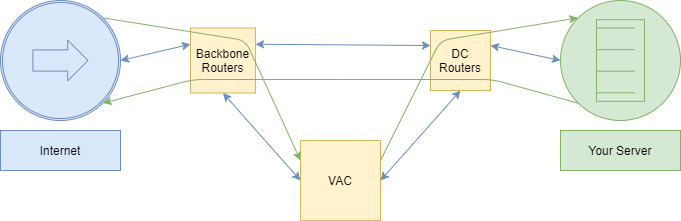
Stage 4: Attack ends
Generating an attack is costly, and even more so when it is ineffective. After a certain time has passed, the attack will come to an end. Auto-mitigation is maintained for 24 hours after the attack has ended. This means any new attack that occurs within a few minutes, a few hours, or 24 hours will be blocked. After just 24 hours, auto-mitigation is disabled but remains ready to be reactivated upon detection of a new attack.
Solution
To effectively deal with such attacks, OVH has developed a state of the art Anti-DDOS technology. It works like this:
Analyze
1/2000 of the traffic is analyzed by backbone routers in terms of “bytes per second” and “packets per second”. Subsequently, the system makes a comparison between the database signature and the samples. Mitigation is immediately activated if the results are positive. All these processes occur instantaneously.
Vacuum
DDoS attacks are aimed at overwhelming servers with an enormous amount of traffic. Because of its high network capacity, VAC System is capable of absorbing multiple attacks over a long period of time. This level of performance cannot be achieved by other providers. The most remarkable thing is that all of this occurs silently and does not in any way interrupt the activities of other customers.
Mitigate
The VAC is where mitigation is done, and it is made up of a Pre-Firewall, Firewall, Shield and Armor. As soon as a DDoS attack is identified, traffic is spontaneously diverted to the VAC. The VAC is designed to filter out compromised traffic and allow only genuine traffic through its filters.
The VAC
The VAC consists of 4 stages and multiple devices. Pre-Firewall, Firewall, Shield and Armor. Each stage is meant to provide different defence strategy, while at the same functioning in unison, to filter even the largest DDOS attacks.
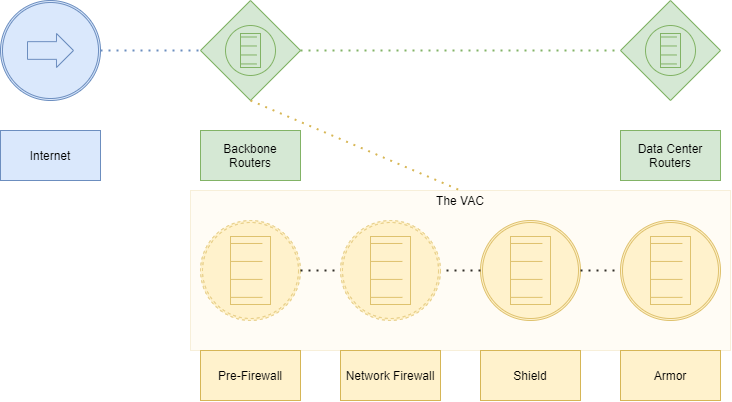
Pre-Firewall Actions
- Fragment UDP
- Authorize/block a protocol
- Authorization of TCP, UDP, ICMP, GRE protocols
- Blocking all other protocols
Firewall Actions
- Authorize/block an IP or a sub-network of IPs
- Authorize/block a port or TCP/UDP port interval
- Authorize/block SYN/TCPs
- Authorize/block all packets except SYN/TCPs
Shield Actions
- Malformed IP header
- Incorrect IP checksum
- Incorrect UDP checksum
- ICMP limitation
- Incorrectly fragmented UDP datagram
- DNS amp
Armor Actions
- Malformed IP header
- Incomplete fragment
- Incorrect IP checksum
- Duplicated fragment
- Fragment too long
- IP/TCP/UDP/ICMP packet too long
- Incorrect TCP/UDP checksum
- Invalid TCP flags
- Invalid sequence number
- Zombie detection
- TCP SYN authentication
- DNS authentication
- Badly formed DNS request
- DNS limitation
Information and schematics were modified and (partly) taken from
our main DDOS protection
provider OVH. We use them for direct and GRE protection.
The information listed
here was public on
their DDOS documentation page. If you need more information about
this technology please refer to that page.